
 It's been known for a month now the NSA exploits released by the Shadow Brokers hacking group could be used to hack almost every pre-Windows 10 system which wasn't patched in March, yet our government and others did nothing. It's been known for a month now the NSA exploits released by the Shadow Brokers hacking group could be used to hack almost every pre-Windows 10 system which wasn't patched in March, yet our government and others did nothing.
Sure enough, the inevitable has now happened.
From RT:
A zero-day vulnerability tool, covertly exploited by US intelligence agencies and exposed by the Shadow Brokers hacking group has been blamed for the massive spread of malware that infected tens of thousands of computer systems globally.
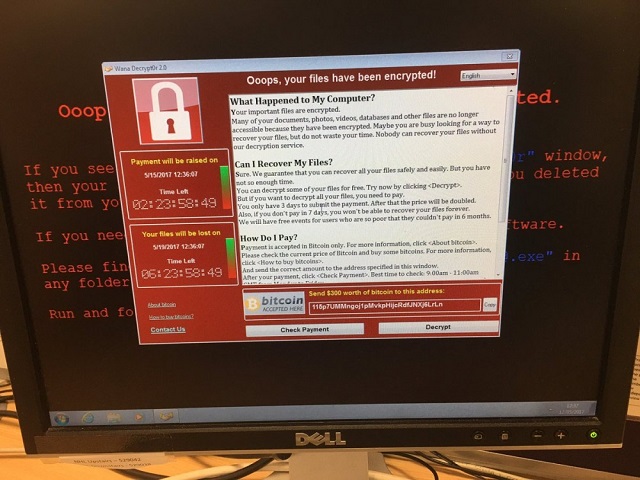
The ransomware virus which extorts Windows users by blocking their personal files and demanding payment to restore access, allegedly exploits a vulnerability that was discovered and concealed for future use by the National Security Agency (NSA), according to a range of security experts.
“Our analysis indicates the attack, dubbed “WannaCry”, is initiated through an SMBv2 remote code execution in Microsoft Windows. This exploit (codenamed “EternalBlue”) has been made available on the internet through the Shadowbrokers dump on April 14th, 2017,” Russian cybersecurity firm, Kaspersky Lab, wrote in a blog post about the attack.
Although Microsoft had already patched the backdoor roughly a month before it became public, many users who did not install the latest security updates seem to have become the primary victims of the attack.
Meanwhile, NSA whistleblower Edward Snowden has led the discussion on NSA’s role and responsibility in Friday’s extensive cyberattacks, noting that if the NSA had “privately disclosed the flaw used to attack hospitals when they found it, not when they lost it, this may not have happened.”
Snowden noted that the NSA developed these “dangerous attack tools that could target Western software” despite warnings, and that it’s now up to congress to question the agency on its knowledge of any other software vulnerabilities.
Wikileaks also referred to its dealings with the whistleblower behind its Vault 7 CIA releases who warned of the extreme proliferation risk in the creation of cyber weapons.
The impact the cyberattack has had on hospitals has raised the greatest concerns. Some 39 hospital trusts as well as GP practices and dental services in the NHS system were targeted across England and Scotland.
The worm has also reportedly hit universities, a major Spanish telecom, FedEx, and the Russian Interior Ministry.
Bruno Kramm, the chairman of the Berlin branch of the Pirate Party told RT that a lot of vulnerabilities lie in the backdoors built into operating systems.
“But the sad thing is the more we find out [about] the NSA having this software, the more we also know that this software is also of course traded. There is no software which you can keep inside of the system. This is why you're supposed to patch backdoors immediately in the interest of national security rather than exploit them for years to hack Middle Eastern banks.
Follow InformationLiberation on Twitter and Facebook.
|






 It's been known for a month now the NSA exploits released by the Shadow Brokers hacking group could be used to hack almost every pre-Windows 10 system which wasn't patched in March, yet our government and others did nothing.
It's been known for a month now the NSA exploits released by the Shadow Brokers hacking group could be used to hack almost every pre-Windows 10 system which wasn't patched in March, yet our government and others did nothing.


